Review: What is Firefox Focus?
You've heard of Firefox, but have you heard of Firefox Focus?
Firefox Focus isn't necessarily new to the game, but it has made quite the name for itself in the privacy community.
Despite that, people want to know how it stacks up in the niche of privacy browsers.
Let's take a look at what Firefox Focus has to offer.
Overview
This is Firefox Focus at a glance...
PROS
- Always on private browsing
- Custom search engines ()
- Safari integration
- Light on system resources
- Responsive user interface ()
CONS
- Lacks "standard" browser features such as tab management
- No dedicated Javascript blocking ()
- No whitelisting feature
- No extension compatibility (not applicable to iOS)
What is Firefox Focus?
Firefox Focus is an official fork of the original Firefox browser that is developed by Mozilla.
(If you're interested, I compared Firefox and Focus in a separate post.)
Officially, Focus debuted in late 2015 as a dedicated tracker blocker for iOS devices.
It didn't become its own standalone browser until 2016.
Additionally, it's considered a no-frills minimalist mobile browser - there is no desktop version of Firefox Focus like there is with regular Firefox.
Mozilla says that Firefox Focus will let you "take private browsing to the next level" and describes Firefox Focus as a "dedicated privacy browser."
Mozilla also says you can use Focus as either a privacy browser or a content blocker for Safari on compatible iOS devices.
We'll evaluate these statements later on in this review.
Download Firefox Focus (iOS) Download Firefox Focus (Android)
Before downloading
Availability
Firefox Focus is only available for mobile platforms. You can find it on iOS and Android.
Be aware that access to Firefox Focus may be restricted in some parts of the world.
Requirements
iOS: You need iOS 11.0 or later to use this browser.
Android: You need Android version 5.0 (Lollipop) or later to use this browser.
App size
The size of Firefox Focus varies on different Android devices.
According to its Apple App Store page, the size of the app is about 14.5MB.
(Even with the Android variance, I can imagine the size isn't too much different between Android and iOS devices.)
Launch and set up
There's super minimal set up necessary before using Firefox Focus.
On the first opening of the browser, you're presented with 3 screens.
These screens give you some insight into what Firefox Focus does and some tips on how to start using it.
Features
We'll dive into the privacy and security features of Firefox Focus. We'll also cover any other cool, notable, or unique features found.
Privacy
Always on private browsing
Firefox Focus is always in "private browsing" mode.
When you quit the browser, it wipes all data such as cookies and browsing history.
Ultimately, that means that Firefox Focus doesn't save any type of data between browsing sessions. You get a fresh and clean start every time you load up the browser.
Tracker blocking
Firefox Focus has good tracker blocking.
From the jump it's set to block ad, analytics, and social trackers. You have the option of blocking "other content trackers," though the app doesn't specify what those are.
Its ad tracker blocking is robust enough that it can block a lot of ads, despite not having a true ad blocker.
size=24 Search options[/size]
You've got a couple of default options for search engines while using Firefox Focus.
Of these listed defaults, I highly suggest using DuckDuckGo. DuckDuckGo is a US based private search engine.
If you want to add a different search engine - which Firefox Focus allows you to do - then I suggest adding a private search engine. We did the leg work and found some of the best private search engines here.
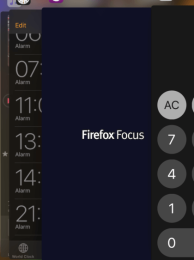
Blank view in app switch
This is a neat little feature Firefox Focus has:
Notice how you can kind of see the screen for my calculator and clock apps.
However, you'll also notice that you can't see what I was last doing or viewing in Firefox Focus.
Security
App lock
You can lock Focus when it's in the background or when it's closed.
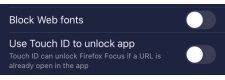
Unlocking the app depends on your device. For example, when Focus has been locked in iOS, you can use TouchID or FaceID to unlock it for use.
There isn't an option for setting a passcode that is independent of how you lock your phone.
So if someone can get into your phone via biometrics such as TouchID, then they can also access Focus even with this the app lock function enabled.
Browser engine
Android: Firefox Focus used the Blink engine in its early days. It has since switched and currently uses the GeckoView engine.
iOS: Focus uses Apple's WebKit rendering engine. This is true for all browsers in the iOS environment, so there's not much for the developers to do about that.
Updates While Firefox Focus has "fallen out of priority," the browser is still updated regularly.
Regular updates improve quality of life and patch known security vulnerabilities.
Web font blocking
Firefox Focus allows you to block web fonts.
Blocking web fonts stops the sites you visit from downloading fonts onto your device.
This helps some websites load faster.
However, when you have this setting enabled, the tradeoff is that many websites you visit will look weird or not be formatted correctly.
This setting is disabled by default.
Other
Safari integration
This really only applies to iOS users.
As Mozilla advertises, you can utilize Firefox Focus''s content blocking capabilities in Safari.
This integration is limited only to Safari. Firefox Focus can't integrate into any other browser, including regular Firefox.
The integration works well. However, you should keep in mind that you can't see exactly what or how many trackers Firefox Focus blocks in Safari.
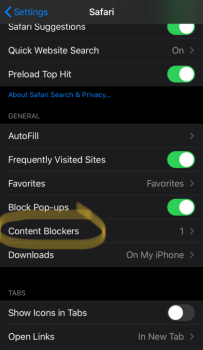
Enabling Safari integration
- Open your Settings app
- Select "Safari"
- Under the "General" settings for Safari, you'll see "Content Blockers"
- Enable Firefox Focus
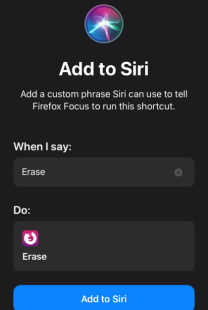
Siri shortcuts
Another thing for iOS users.
Focus allows for the use of Siri shortcuts.
You can set up your shortcuts to erase all data or open a specified website URL.
Hint: Want to be discrete? Then you might want your Siri command to be something other than "Erase."
The GOOD
Responsive UI
Firefox Focus' responsiveness is hard to beat.
The user interface responds blazing quick; there's little "freezing" or "lagging" between commands and execution.
Additionally, the UI is very simple and clean. It's easy to find what you're looking for.
Good privacy defaults
Focus has some of the better privacy defaults, especially when compared with the regular Firefox mobile browser.
By default, Focus blocks ad, analytics, and social trackers.
Its number one default* is that its always in private browsing mode, saving none of your data between sessions.
*Just to reiterate, you can't turn off the private browsing mode.
This comes in handy when you want to browse without being tracked, or without any 3rd party snooping in on what your browsing history is like.
Light on system resources
Firefox Focus is easy on your device's resources.
It's snappy and quick while not draining memory or computing power. You can have more apps open along with Firefox Focus, and switch back and forth between different app windows faster.
It also has an insanely light storage footprint. Firefox Focus doesn't take up a lot of space due to it being a minimalistic browser and not storing data between browsing sessions.
This can prove essential for devices that don't have a ton of raw storage to spare and/or don't utilize cloud-based storage.
The BAD
Missing "standard" browser features
It's important to understand that Firefox Focus was never designed to be a full-fledged browser.
Its sole focus has always been on minimalism and easy-to-configure user privacy. Even though it lacks something as simple as tab management, I personally consider its minimalism a feature.
But I have included it here in the "bad" section because this minimalism alone may be a dealbreaker for some users.
With that said, yes, Firefox Focus lacks many browser features that have simply become "standard."
Some of these common features include:
- Tab management
- Bookmarking
- Browsing history
- Cache/Cookie storage
Absent Javascript blocking
This is one of my biggest pain points with this browser:
There's no option to block all Javascript.
For more savvy users, this alone could be a dealbreaker.
Sketchy sites can use Javascript for malicious reasons. It can make sense why some people would at least want the option of blocking Javascript, even if just temporarily.
While Firefox Focus may block some content that uses Javascript, it will very rarely (if ever) block all Javascript on a page.
No whitelisting
You can't make exceptions to blocking for specific websites while using Firefox Focus.
Focus uses an "all or nothing" approach when it comes to blocking features.
This means that if you want to disable tracker blocking for a website, you'll have to temporarily disable blocking entirely.
That isn't too hard, I admit. The tricky part is remembering to re-enable tracker blocking when you're finished!
If you don't re-enable tracker blocking, you're not getting any protection from invasive trackers.
No extension compatibility (Android)
This only applies to Android users.
While the regular Firefox has extension compatibility, Firefox Focus doesn't.
Final thoughts
The main takeaway from this review is that Firefox Focus is a minimalist browser that makes user privacy its main concern.
And it does that well.
Focus might not be first choice when it comes to replacing Google Chrome or Safari, but it is a decent alternative.
Focus is excellent as a secondary browser, for when you just want to "pick up and go" without having to worry about any frills.
Download Firefox Focus (iOS) Download Firefox Focus (Android)
As always, stay safe out there!