guides

guides
4 Ways to Store Backup Codes, Keys, and Seed phrases
Backup codes, keys, and seed phrases are important if you lose access to multifactor authentication (MFA) methods or are otherwise completely locked out of your accounts.
There are many methods to store backup codes, keys, and seed phrases. Some methods may be better for certain situations and/or...

guides
A Basic Guide to Router and Wireless Security for Regular People
Router and wireless security for the home/small network is often overlooked due to the limitations of consumer grade hardware and general lack of awareness of network security (NetSec).
As such, many users run home or small office networks that introduce a great amount of unnecessary risk.
This...
guides
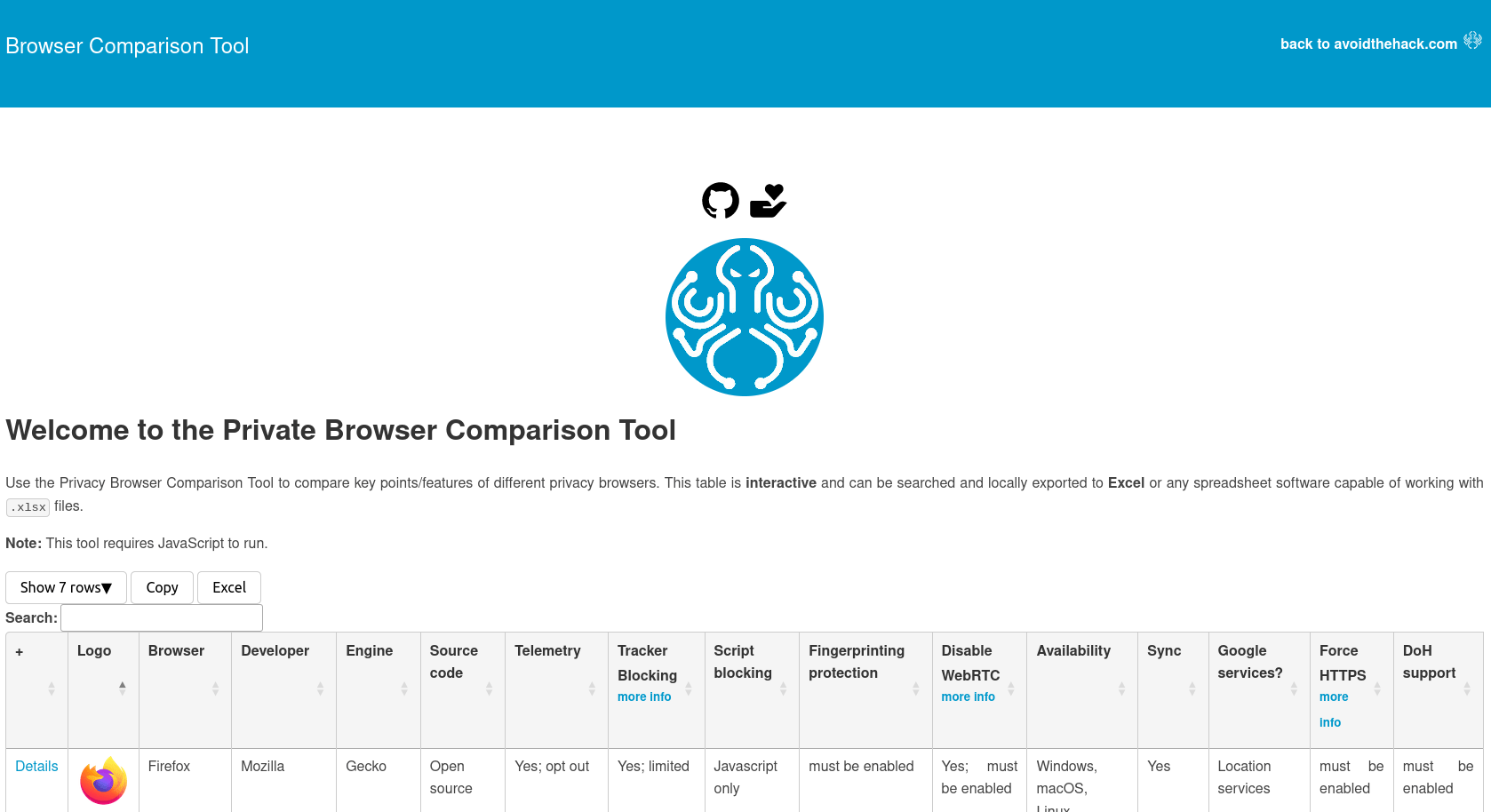
Avoid The Hack: 18 Free and Easy-to-Use Tools to Improve Your Privacy
This post was originally published on 1 SEP 2022; it has since been updated and revised.
One of the biggest sticking points commonly brought up in the privacy community is the price of privacy.
As it generally goes, especially on the internet as a whole, free is not free – however, there are s...

guides
Blocking Ads, Trackers, and Malware in Browsers, Devices, and Networks
This post was originally published on 18 MAY 2022; it has since been updated and revised.
You may hear a lot that you should block ads and trackers, but you may also have a lot of questions, such as (but not limited to):
How can you block ads on your iPhone or Android?
Is it possible t...
guides
Everything You Should Know Before Using a Password Manager
Passwords, passwords, passwords.
We have so many passwords to create and remember, don't we?
According to recent research conducted by NordPass, the average internet user has approximately 70 - 80 passwords to remember.
No matter how you try to slice it, that's a ton of passwords to memorize...

guides
Getting Started: A Beginner's Guide for Improving Privacy
Welcome to the world of online/digital privacy!
Like its sister guide for cybersecurity, this privacy guide was written for complete privacy novices in mind. It is designed to be a starting point for anyone new to the world of online privacy.
It also contains actionable advice for getting sta...

guides
Getting Started: Basic Personal Cybersecurity for Everyone (3 Easy Tips)
This post was originally published on 10 MAY 2023; it has since been updated and revised.
Welcome to the world of cybersecurity!
This guide was written for complete cybersecurity and privacy novices in mind. It is designed to get anyone started on improving their personal cybersecurity, wh...

guides
How (and Why) to Take Full Advantage of Apple’s New Advanced Data Protection Feature
With the iOS 16.2 update, Apple introduced “Advanced Data Protection,” which finally introduced end-to-end encryption (E2EE) for most items backed up or stored in iCloud.
Apple has long been criticized, with good reason, over its iCloud service not providing E2EE (where the user has the decryption...

guides
How to Configure Safari for Privacy on iOS Devices (UPDATED FOR iOS 16.2)
This post was originally published on 2 OCT 2020; it has since been updated and revised.
Though Safari is a closed-source browser, some users may wish to use with their Apple devices.
This how-to guide will show you how to increase your data privacy and security while using Safari. This guide...

guides
How to Find Old Accounts for Deletion
Old accounts are often unmaintained and forgotten - which can be problematic when you want to "clean up" some of your digital footprint by deleting them or go back to secure them with stronger passwords/MFA.
How do you find these old accounts when your recollection isn't enough? Fortunately, we al...

guides
How to Install and Configure PiHole
For a lot of people, the hardest part about running a PiHole is generally setting up the whole thing.
This can be especially true if you're not the best networking person or are unfamiliar with the typical environment (Linux) that PiHole usually calls home.
The aim of this guide is to provide...

guides
How to Install and Configure Ungoogled Chromium
This post was originally published on 7 OCT 2021. It has since been revised and updated.
Long story short: Google Chrome sucks for privacy.
Now, with that out the way, I'm here to show you how to download, install, and tweak the Ungoogled Chromium browser.
Bear in mind that installing and...

guides
How to Install Librewolf
When configured properly, Mozilla Firefox offers great privacy and security.
However, achieving a higher level of privacy and security in Mozilla Firefox requires many tweaks across all levels. Some users may not be too comfortable with this and may prefer an out-of-the-box solution that isn't Chromium dependent.

guides
How to Manually Install Extensions (Ungoogled Chromium)
This post was originally published on 20 NOV 2020; it has since been updated and revised.
For those who don't wish to download Chromium extensions from the Chrome Web Store, there is (fortunately) an alternative: you can install Chromium extensions manually. No Google account required.
While...

guides
How to Use a Password Manager (Beginner Friendly)
Using a password manager can prove highly essential for good password management practices.
Broadly speaking, password managers allow users to generate strong passwords - but most importantly they allow users to have unique passwords for their various online accounts, eliminating the need fo...
guides
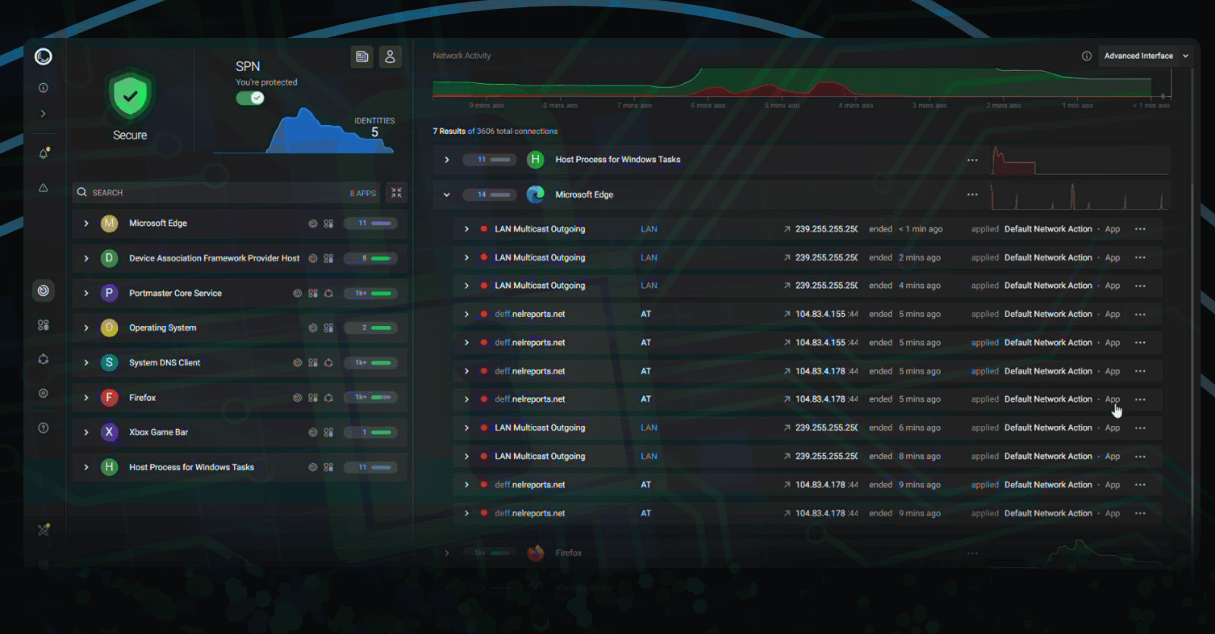
How to: Basics of Using Safing Portmaster
This post was originally published on 1 FEB 2023; it has since been updated and revised.
In this guide we look at how to get familiar with using/tweaking Safing Portmaster, an open-source and host-based application firewall available for Linux and Windows machines.
...

guides
Switching From Twitter to Mastodon
This post was originally published on 7 NOV 2022; it has since been updated and revised. avoidthehack is actively looking for tips/contributions to this guide in future updates.
What is Mastodon?
Mastodon is an open-source and decentralized microblogging network. Mastodon is also part of a lar...

guides
Trusted Tools to Control Windows 10 & 11 Data Collection
Microsoft Windows 10 (and the newer edition, Windows 11) is a data collection machine that phones home a lot.
Some examples of the data Windows collects:
Searches (which get forwarded to Bing, Microsoft's search engine)
Voice data (for devices where a mic is present)
Keystrokes/typing hist...
guides
WebRTC Leaks and Your Privacy (+ how to fix them)
This post was originally published on 31 JAN 2021; it has since been updated and revised.
WebRTC can prove useful when users need to use it, which is most commonly during peer-to-peer (P2P) calling in the browser.
However, a critical flaw yet to be directly and adequately addressed across a...